1 Addressing crosscutting aspects by-design
Various crosscutting aspects (also known as non-functional or quality characteristics) of systems are, actually, dependant on all the system elements and relationships between them. For example, the security design principle “weakest link” is saying that “in designing security for a system, focus should be put on the weakest components of the overall system” (see Goldratt E.M., Cox J. The Goal: A Process of Ongoing Improvement, Second Revised Edition, 1992).
The understanding of emergent nature of crosscutting aspects led to raising of requirements for addressing them “by-design”. The most noticeable example of “privacy by-design” is the General Data Protection Regulations (GDPR) from the European Union (see https://eur-lex.europa.eu/eli/reg/2016/679/oj ). The concept “a system characteristic by-design” may be defined as “taking into account the characteristic throughout the system entire lifecycle processes (e.g. architecting, engineering, construction, operating, etc.) as an essential emergent characteristic of the system”.
2 Security Risk Architecture Model (SRAM)
To “estimate” a relative value of a non-functional or quality characteristic of a system at any stage of the system life cycle, it is necessary to “spread” such characteristic over the system elements and relationships between them. Figure below shows, that by knowing:
- the security-related paraments, i.e. threats, attacks and vulnerabilities (see oval “Security”) for each least granular system elements;
- relationships between the system elements (see oval “Architecture”), i.e.
- how a set of least granular elements forms a service,
- how services are used in business processes,
- how business processes contribute into results,
- how results reflect goals,
- how goals are important for the system;
- adverse impact which is produced by problems with each system element;
Considering that relationships between system elements are static or dynamic then the structure and behaviour of security will be covered. The same can be done for all crosscutting aspects: security, privacy, safety, reliability, resilience, performance, value, income, expenses and other emergent characteristics.
3 Enhancement practices
There are internal and external enhancement practices for each crosscutting aspect. The internal enhancements practices comprise various certifications and industry agreements which are aspect-specific and element-specific. The external enhancement practices depend on the treatment of an element as:
- “white-box” with fully internal visibility and testability – some simulation, inspection and compliance external enhancement methods can be used;
- “black-box” with no internal visibility and testability – use external enhancement points for data/information inputs and outputs, and external enhancement controls for leaks detection;
- “grey-box” with partial internal visibility and testability – combining two previous options.
Typically, external enhancement methods are based on explicit relationships between elements (e.g. information flows). External enhancement points are based on digital archives and technologies similar to Security Information and Event Management (SIEM) tools. External enhancement controls are monitoring tools with some AI logic, for example, Data Loss Protection (DLP) tools.
For each relationship between elements, use external enhancement points for data/information flow starts and ends, and external enhancement controls for data/information transit.
The static relationships are expressed by any structural connection between elements, but dynamic relationships are expressed only by events (ECA and EPN techniques), processes (BPM techniques) and information flows (IFD techniques).
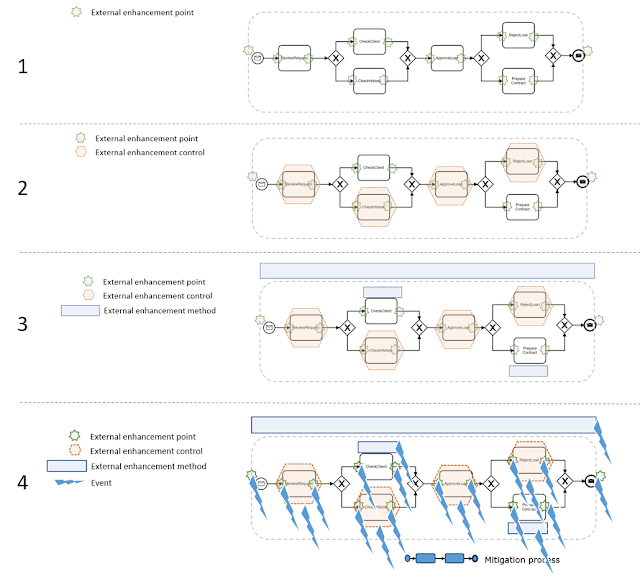
For example, a process model formally identifies all necessary enterprise enhancement points, methods and controls. (see figure below)
- Add all external enhancement points.
- Add all external enhancement controls for 4 activities which are “black-boxes”.
- Add all external enhancement methods for 2 activities which are “white-boxes” and the process as the whole.
- Add all the events and mitigation processes for some of them.
Thus, an explicit description of system elements and relationships between them provides a nomenclature of external enhancement practices, controls, points, and methods to be added to the system. Then they have to be linked to the risk management practices. All the information risk-related information sourced from various crosscutting aspects must be collected and treated together (see figure below).
- Enterprise business functions should be enriched to generate the risk-related information.
- Those risk-related data need to be collected at the enterprise data warehouse together with other business information.
- Some business processes need to be updated to embed risk-related activities.
- A set of risk-related rules, logic and risk-related knowledge should be able to use the risk-related and other business data to detect acceptable limits of risk as well as interdependencies and correlations between different risks.
- Some business processes for risk mitigation maybe automatically activated.
- A lot of risk-related indicators, alerts should be available in the form of dashboards and reports available for different staff members.
- Staff members should be able to initiate business processes based on the observed risk-related information.
Additional security-related techniques are mentioned in https://improving-bpm-systems.blogspot.com/2014/04/ideas-for-bpmshift-delenda-est-vendor.html
4 Conclusion
Crosscutting aspects are desired emergent characteristics of a system. They must be addressed systemically.
Thanks,
AS
This blogpost belongs to the series https://improving-bpm-systems.blogspot.com/search/label/%23BAW